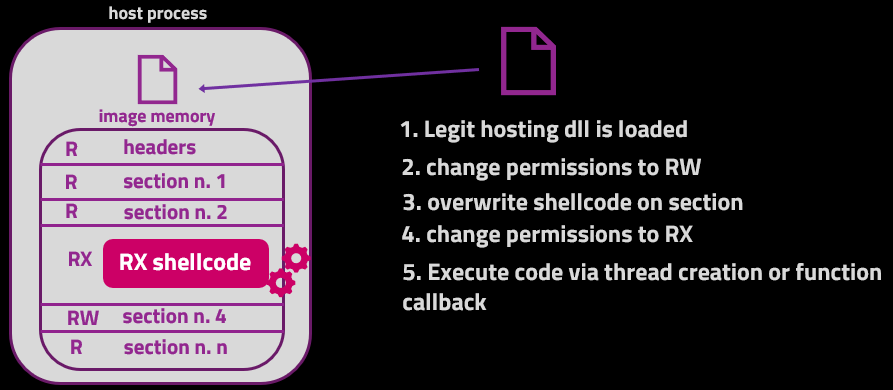
ModuleShifting - Stealthier Variation Of Module Stomping And Module Overloading Injection Techniques That Reduces Memory IoCs
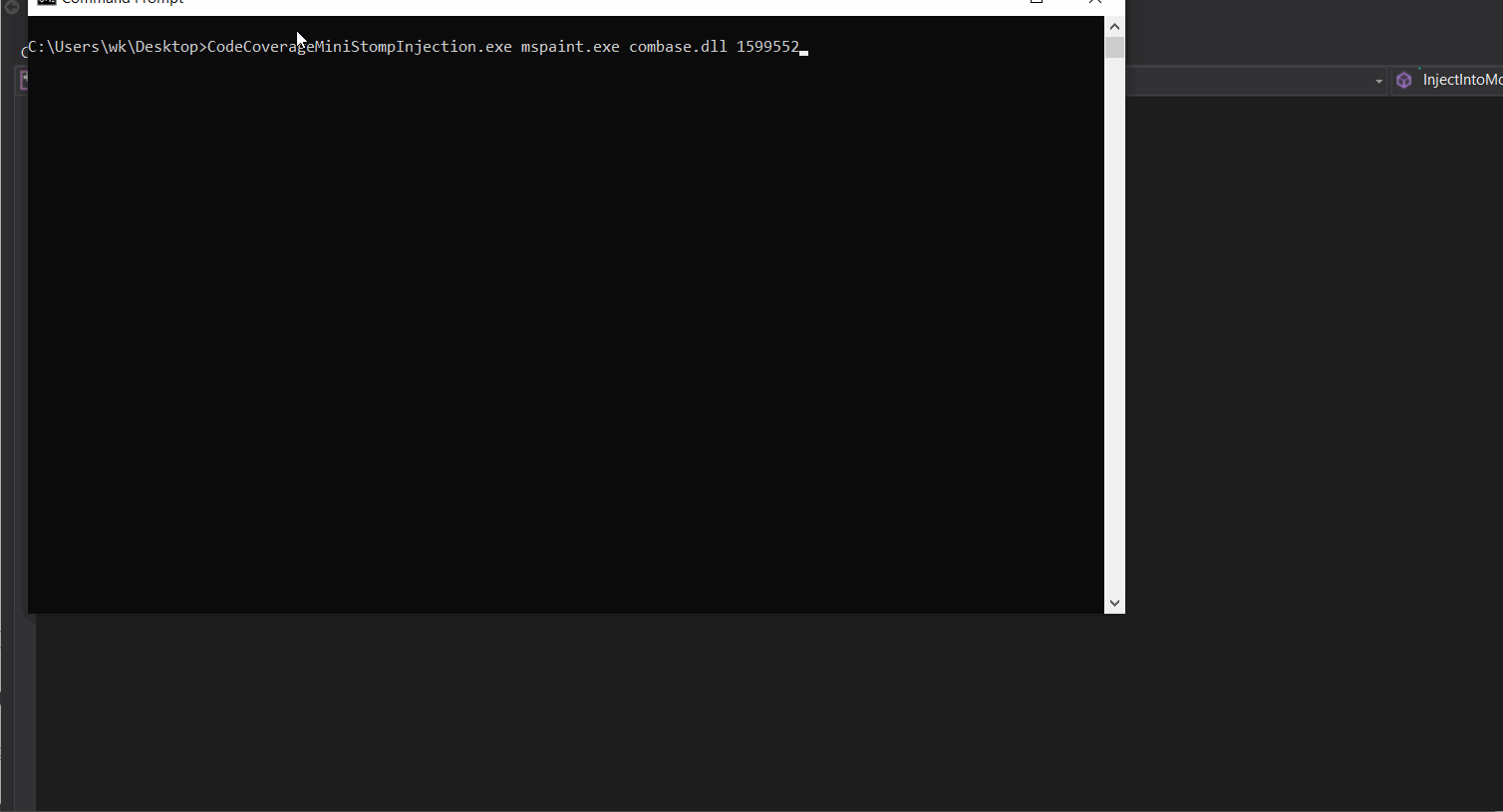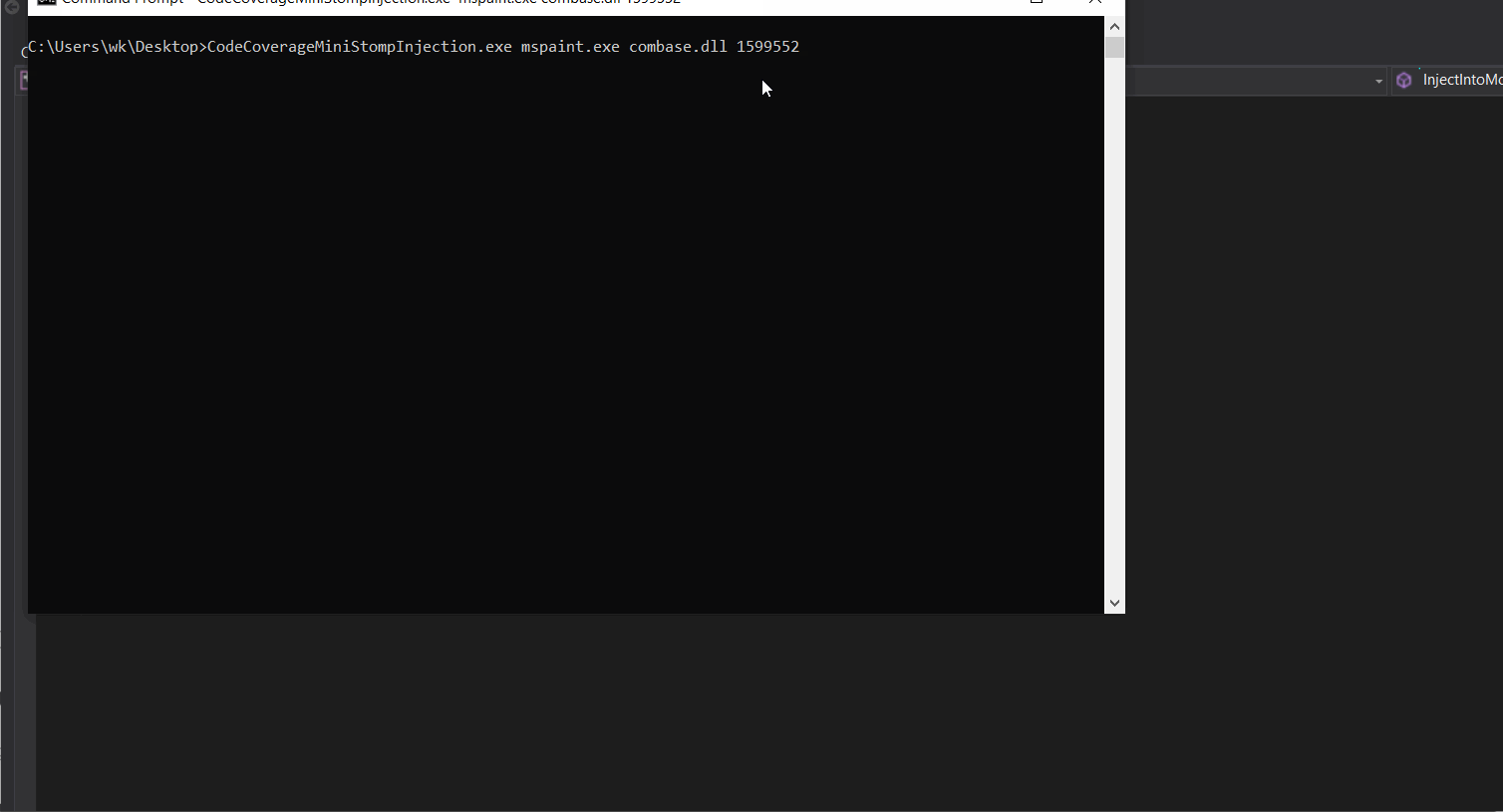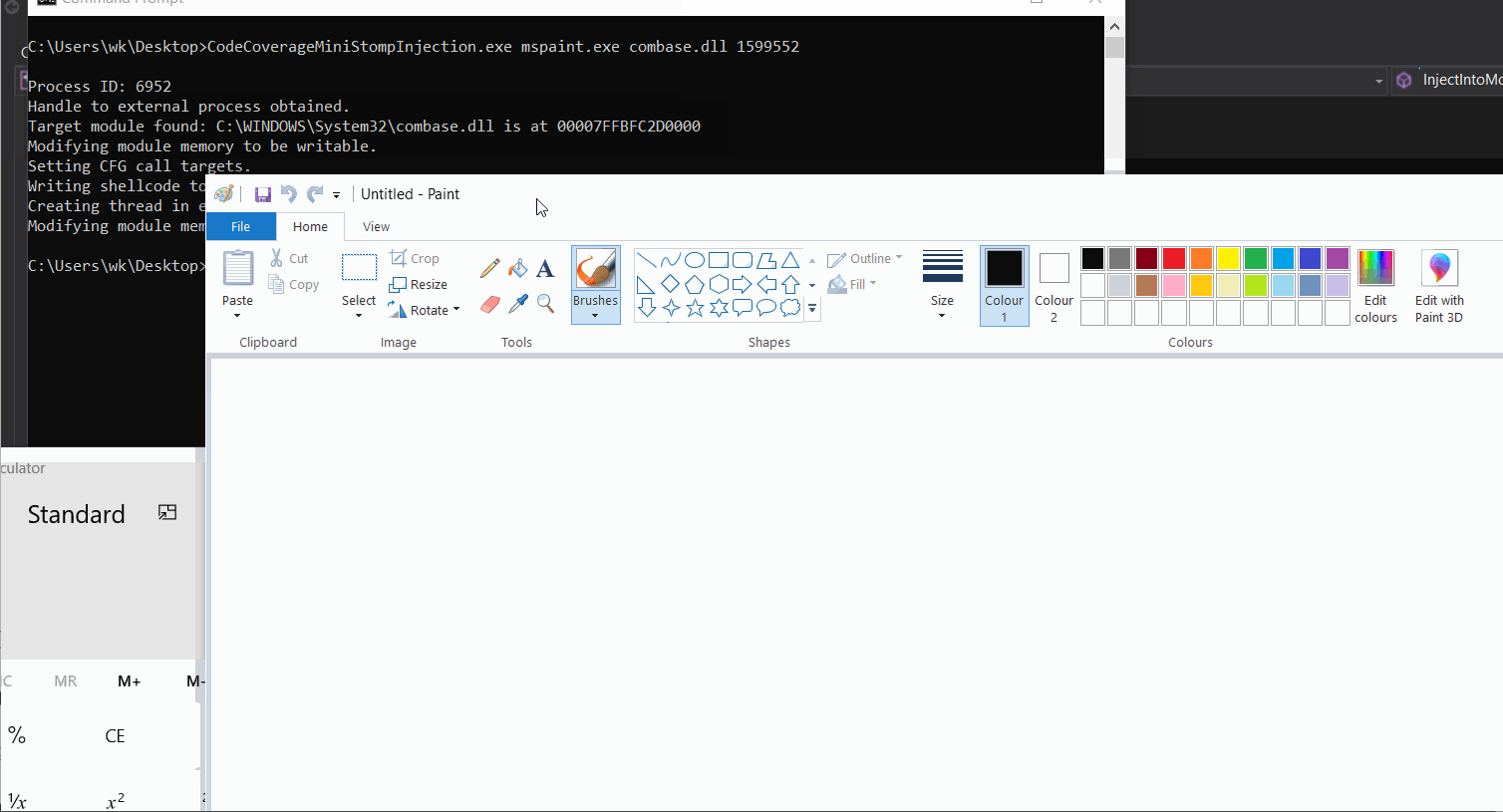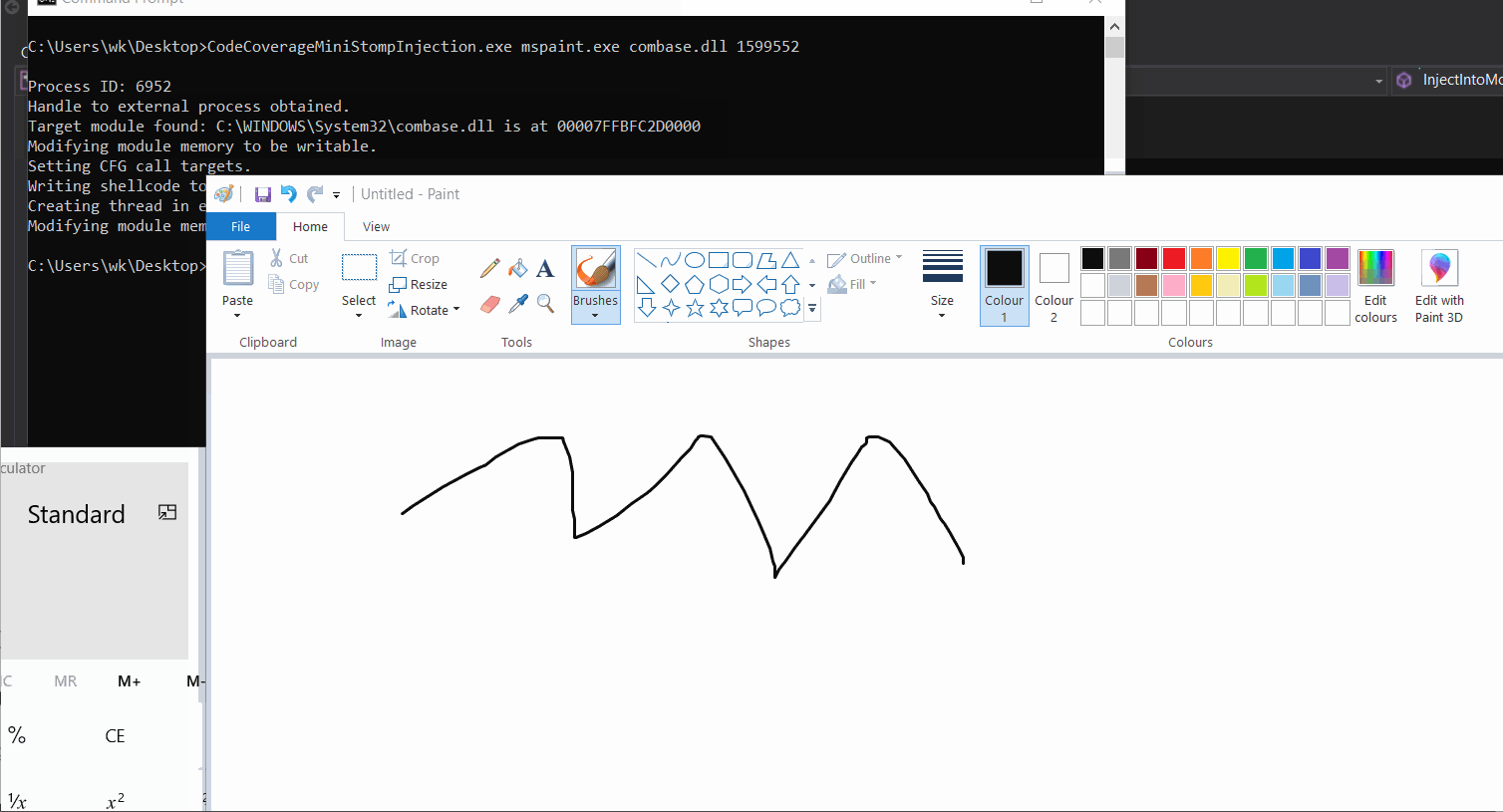
Living Dangerously with Module Stomping: Leveraging Code Coverage Analysis for Injecting into Legitimately Loaded DLLs - ...

Matthew on X: "I've been playing around with Module Stomping for EDR Evasion This is a cool technique for bypassing detection by overwriting "legitimate" memory regions. Let's see what it looks like

HackGit on X: "ModuleShifting Stealthier variation of Module Stomping and Module Overloading injection techniques that reduces memory IoCs. Implemented in Python ctypes. https://t.co/tktzbr5GqF #infosec #pentesting #redteam https://t.co/Tuf0hT779Z ...